Android Malware and Analysis: Dunham, Ken, Hartman, Shane, Quintans, Manu, Morales, Jose Andre, Strazzere, Tim: 9781482252194: Amazon.com: Books
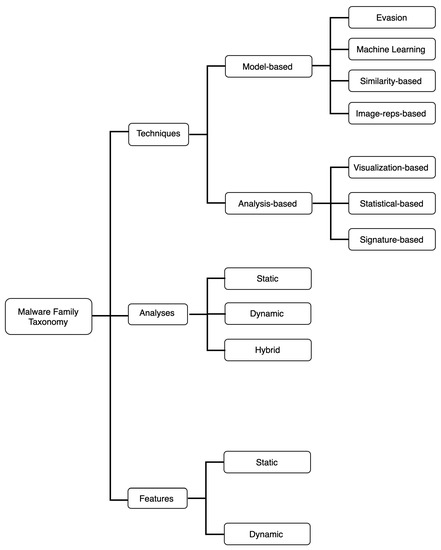
Electronics | Free Full-Text | Android Malware Family Classification and Analysis: Current Status and Future Directions | HTML

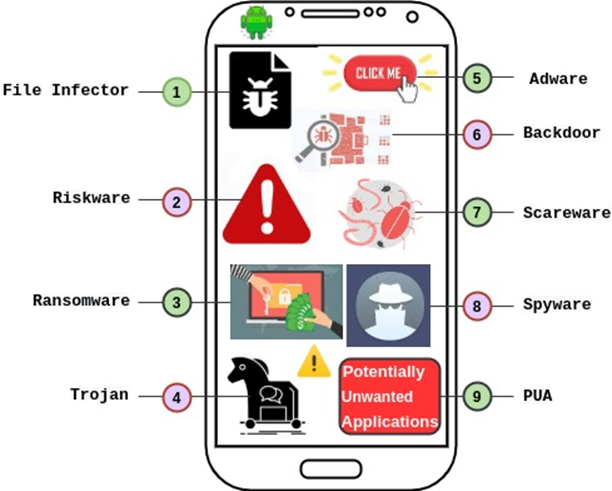
View of A Review on Android Malware: Attacks, Countermeasures and Challenges Ahead | Journal of Cyber Security and Mobility
![Malware detection using static analysis in Android: a review of FeCO (features, classification, and obfuscation) [PeerJ] Malware detection using static analysis in Android: a review of FeCO (features, classification, and obfuscation) [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2021/cs-522/1/fig-1-full.png)