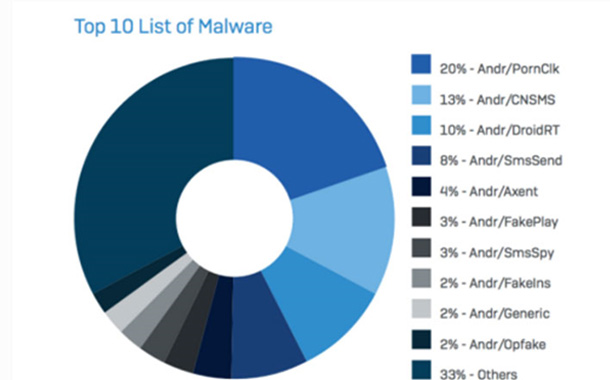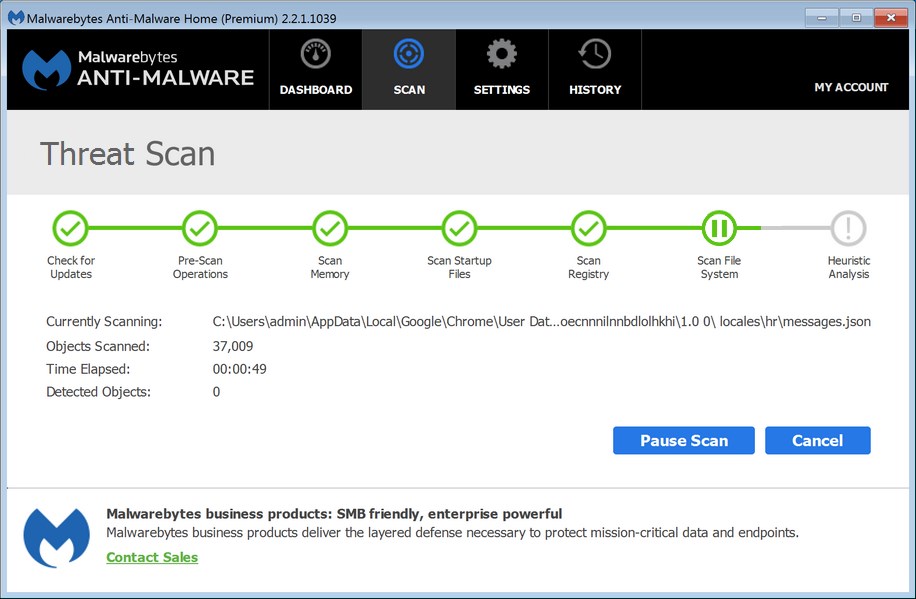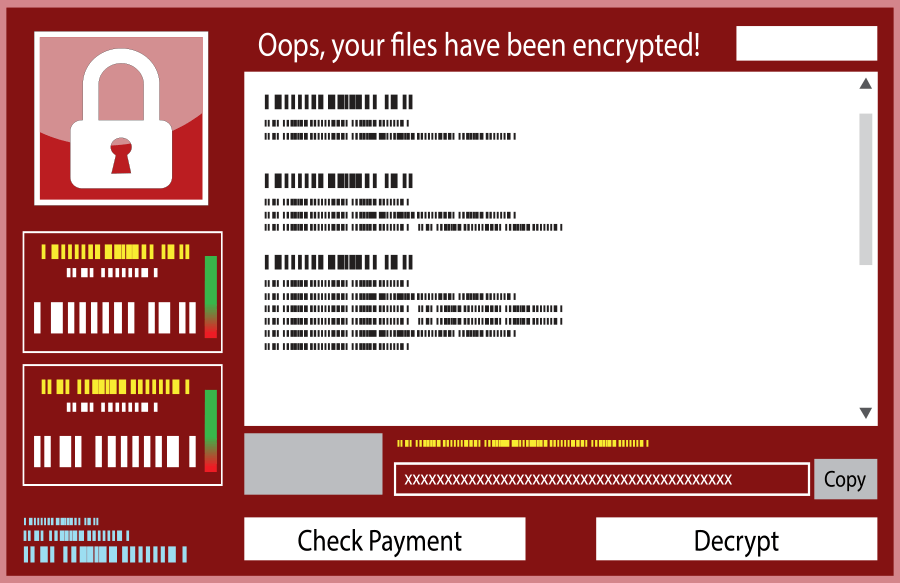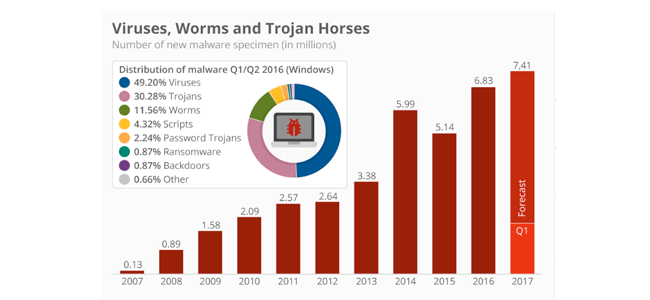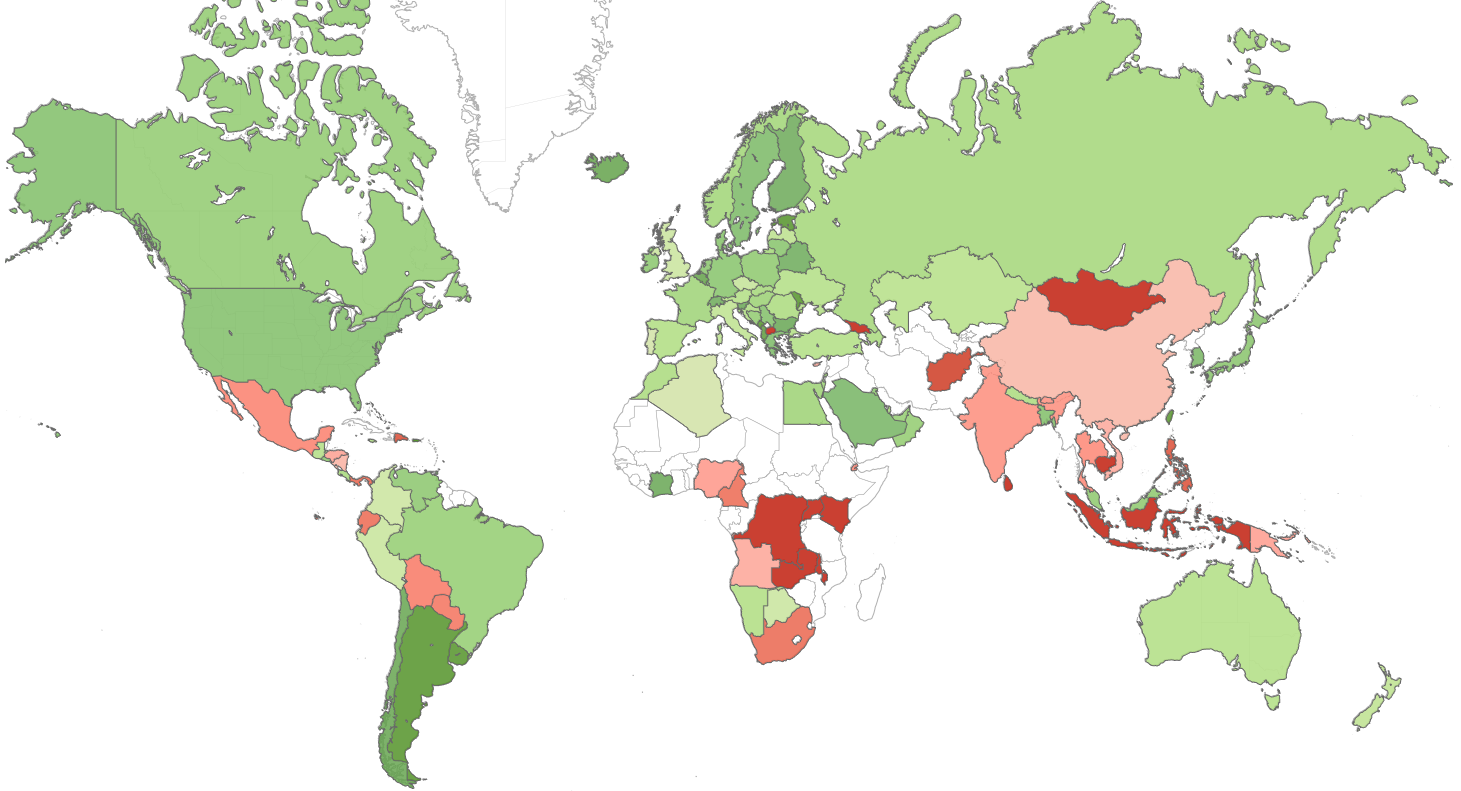
Hancitor Makes First Appearance in Top Five 'Most Wanted' Malware in Check Point's February Global Threat Impact Index - Check Point Software

Carbon Black 2017 Threat Report: Non-Malware Attacks and Ransomware Continue to Own the Spotlight - The Tech Revolutionist
![Top 8 network attacks occur in 2017 till June [Source: McAfee Labs, 2017] | Download Scientific Diagram Top 8 network attacks occur in 2017 till June [Source: McAfee Labs, 2017] | Download Scientific Diagram](https://www.researchgate.net/profile/Ajeet-Singh-16/publication/325330593/figure/fig3/AS:813054006677504@1570858589217/Top-8-network-attacks-occur-in-2017-till-June-Source-McAfee-Labs-2017.jpg)
Top 8 network attacks occur in 2017 till June [Source: McAfee Labs, 2017] | Download Scientific Diagram
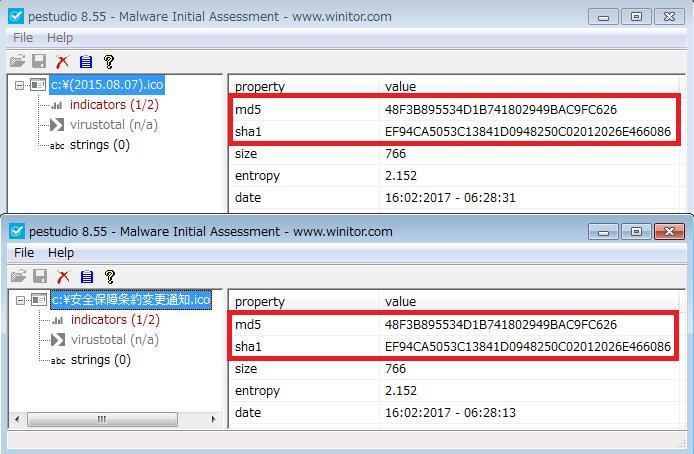
The Relationship Between the Attack Group menuPass and Malwares "Poison Ivy, PlugX, ChChes" | LAC Co., Ltd.
![Top Malware attack in quarter 2 nd , 2017 [Source: McAfee Labs, 2017]. | Download Scientific Diagram Top Malware attack in quarter 2 nd , 2017 [Source: McAfee Labs, 2017]. | Download Scientific Diagram](https://www.researchgate.net/profile/Ajeet-Singh-16/publication/325330593/figure/fig4/AS:813054006673409@1570858589244/Top-Malware-attack-in-quarter-2-nd-2017-Source-McAfee-Labs-2017.jpg)


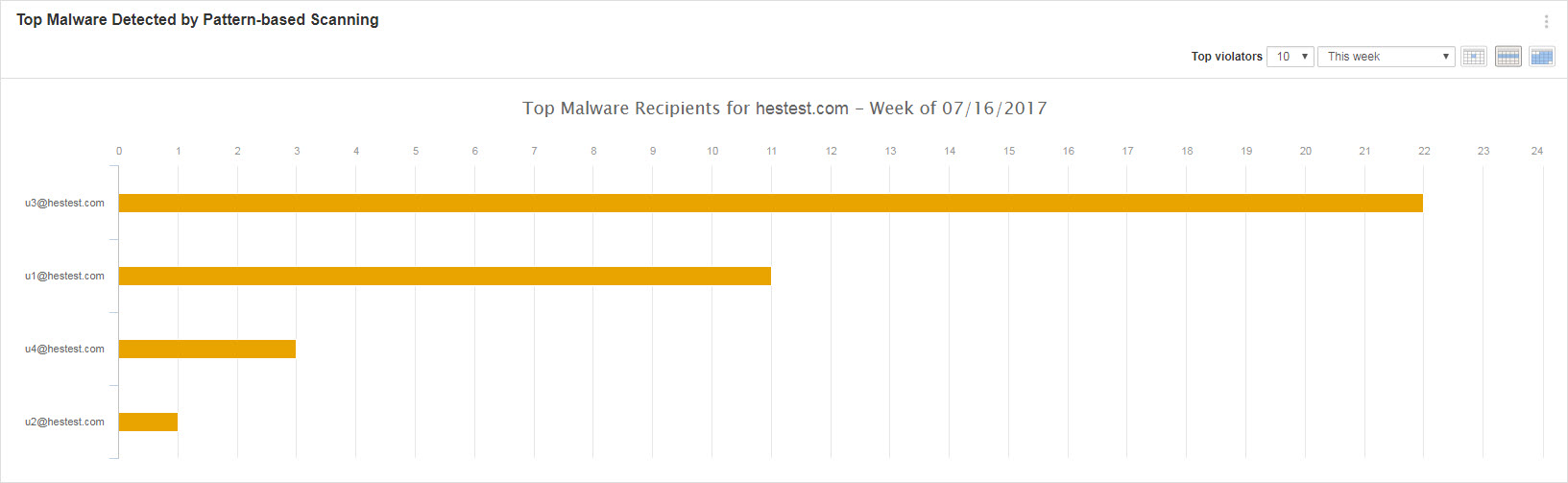




![Top 10 Ransomware Attacks of 2017 [Infographics] - VinRansomware Top 10 Ransomware Attacks of 2017 [Infographics] - VinRansomware](https://www.vinransomware.com/images/blogs/13-11-2017/Top-10-Ransomware-Attacks-of-2017.jpg)